TUT:Security
Contents
SNMPv1 and SNMPv2c: Insecure!!!
SNMP, when it was first developed, contained clear-text-"passwords" called "community strings". The first two versions of the SNMP protocol (SNMPv1 and SNMPv2c) contained these clear text passwords, as can be seen below in the following screen dump:
# snmpget -d -v 2c -c demopublic test.net-snmp.org sysContact.0 Sending 47 bytes to UDP: [157.185.82.8]:161->[0.0.0.0]:0 0000: 30 2D 02 01 01 04 0A 64 65 6D 6F 70 75 62 6C 69 0-.....demopubli 0016: 63 A0 1C 02 04 78 8E 32 C9 02 01 00 02 01 00 30 c....x.2.......0 0032: 0E 30 0C 06 08 2B 06 01 02 01 01 04 00 05 00 .0...+......... Received 102 byte packet from UDP: [157.185.82.8]:161->[0.0.0.0]:47960 0000: 30 64 02 01 01 04 0A 64 65 6D 6F 70 75 62 6C 69 0d.....demopubli 0016: 63 A2 53 02 04 78 8E 32 C9 02 01 00 02 01 00 30 c.S..x.2.......0 0032: 45 30 43 06 08 2B 06 01 02 01 01 04 00 04 37 4E E0C..+........7N 0048: 65 74 2D 53 4E 4D 50 20 43 6F 64 65 72 73 20 3C et-SNMP Coders < 0064: 6E 65 74 2D 73 6E 6D 70 2D 63 6F 64 65 72 73 40 net-snmp-coders@ 0080: 6C 69 73 74 73 2E 73 6F 75 72 63 65 66 6F 72 67 lists.sourceforg 0096: 65 2E 6E 65 74 3E e.net> SNMPv2-MIB::sysContact.0 = STRING: Net-SNMP Coders <net-snmp-coders@lists.sourceforge.net>
This was obviously a problem so SNMPv3 was later developed to secure the protocol.
SNMPv3: Making it secure
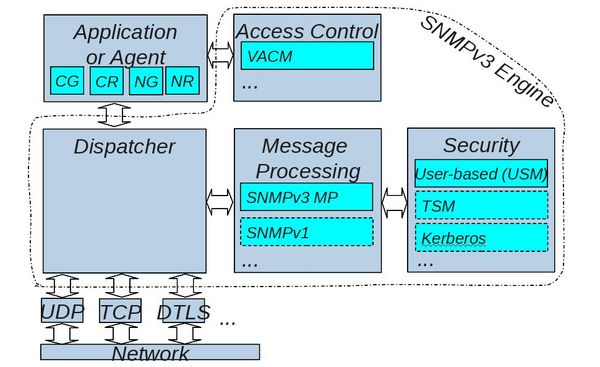
SNMPv3, documented in RFCS 3410-3419, defines a modular approach to SNMPv3. This modular approach is important as it is designed to allow the protocol to adapt in the future if other types of security will be needed or preferred.
Using Secure SNMP
Choices for securing SNMP include, which are described in detail below:
| SNMPv1 or SNMPv2c | Provides NO SECURITY at all. Supported by everything. |
| SNMPv3 with USM | The original SNMPv3 security model. Supported by most devices. |
| SNMPv3 with TLS or DTLS | Tunneling SNMP over TLS and DTLS. Hopefully supported by most devices soon. |
| SNMPv3 over SSH | Tunneling SNMP over SSH (not 100% supported in Net-SNMP) |
| SNMP over Kerberos | Securing SNMP with Kerberos (even less supported) |
Ok, but what should I pick?
Pick the best one for your situation of course! Some helpful starting hints though:
- If entirely using Net-SNMP products, or products that support TLS: use SNMPv3 over (D)TLS
- If talking to legacy SNMPv3 devices: use SNMPv3/USM
- If talking to SNMPv1/SNMPv2c only devices: call the vendor and complain! Seriously.
SNMPv3 with USM
The original SNMPv3 specifications included a User-Based Security Model which secured the protocol by allowing administrators to define "users" with various security credentials. This went a long way toward securing the protocol (although, as Wes Hardaker (the founder of Net-SNMP) documents on a blog entry, there are still some concerns with SNMPv3/USM). Operators also found that securing SNMPv3/USM required "yet another" password database to maintain which was operationally burdensome.
SNMPv3/USM is fairly widely implemented and most modern "good" devices will support it.
See our SNMPv3/USM tutorial for details on using SNMPv3/USM with the Net-SNMP toolkit.
Tunneling SNMPv3
The most recent IETF activity regarding SNMP security has been done in the Integrated Security Model for SNMP (ISMS) working group. Rather than create another security system like USM did, it was decided that users would prefer to tunnel SNMP over protocols they already knew and understood. This was done by creating the following new RFCs:
- RFC5590 - Transport Subsystem for the Simple Network Management Protocol
- RFC5591 - Transport Security Model for the Simple Network Management Protocol (SNMP)
- RFC5592 - Secure Shell Transport Model for the Simple Network Management Protocol (SNMP)
- RFC5608 - Remote Authentication Dial-In User Service (RADIUS) Usage for Simple Network Management Protocol (SNMP) Transport Models.
- RFC5953 - Transport Layer Security (TLS) Transport Model for the Simple Network Management Protocol (SNMP)
These RFCs provide the framework for tunneling SNMPv3 packets over SSH, TLS and DTLS. The SSH protocol uses existing SSH authentication and encryption methods (like SSH keys and/or usernames and passwords) to secure it's traffic. And the TLS and DTLS protocols use X.509 certificates for securing it's traffic.
Net-SNMP 5.6 contains robust support for using SNMP over TLS and DTLS.
See the Using TLS tutorial for details on seting up and using SNMP over TLS and DTLS.
Net-SNMP 5.6 also contains minimal support for using SNMP over SSH, but the support is limited because of the lack of available SSH server-side libraries and is implemented through a specialized shell "hack" when attached to a OpenSSH sshd server.
There is information about the performance impacts of using SSH available here (also available as slides from an IETF presentation here).
Kerberos SNMPv3
Wes Hardaker and Ken Horstein started work in the IETF to implement a kerberos security model for SNMPv3. Although Net-SNMP contains a prototype implementation of this, the work was never finished within the IETF nor within the Net-SNMP implementation and is not yet ready for real-world use.